Vulnerability Assessment & Penetration Testing
What is VAPT?
Why do you need VAPT Testing Services?
01
For Business needs
It is becoming common practice today for customers to request Security Certifications from their partners or vendors. Engaging a trusted VAPT service provider ensures you meet these requirements while offering comprehensive security monitoring that extends beyond assessments.
02
For Security validation
Vulnerability Assessment & Penetration Testing (VAPT) helps validate your security controls and measures against real-world attacks through validations like Application Penetration Testing and Infrastructure VAPT, as well as more advanced simulations.
03
For Compliance
A large number of industry standards & regulations have included Vulnerability Assessment & Penetration Testing Services as a mandatory requirement.
04
For Best-practice & data security
As attackers scale and threats evolve, there is a need within organizations to carry out proactive security audits to protect their data and systems from evolving threats, alongside continuous threat detection and response.
Protecting the world's top innovators




Scope of VAPT Testing
Compliance Standards & Certifications
- Compliance standards that require periodic VAPT services include:
- ISO 27001 | PCI DSS | SOC 2 | HIPAA | GDPR
- CERT-In | FISMA | NIST | SAS 70 | COBIT | OWASP
Our Security Qualifications





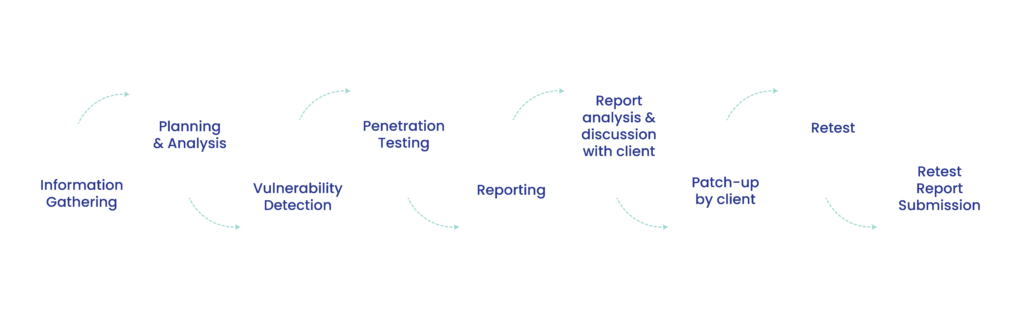
VAPT Methodology
Types of VAPT Services We Offer
Here are the different types of VAPT services
Network Penetration Testing
Scans for vulnerabilities in network infrastructure, such as routers, switches and firewalls to rectify misconfigurations and weak security policies.
Web Application Security Testing
Website penetration testing evaluates the security of web applications, including websites and web-based portals in search of activities like SQL injection, cross-site scripting (XSS) and cross-site request forgery (CSRF).
Mobile Application Penetration Testing
Carries out VAPT for mobile apps, including iOS pen testing and Android application penetration testing to identify weak points in app code, data storage and network communication.
Cloud Penetration Testing
Evaluate the security of cloud environments, including infrastructure as a service (IaaS), platform as a service (PaaS) and software as a service (SaaS) to strengthen cloud configurations, access controls and data storage.
IoT Penetration Testing
Evaluates the security of IoT devices, such as smart home devices and industrial control systems covering device firmware, network communication and data security. Contact us today to schedule a VAPT assessment.
Awards & Recognitions

